How to get IIS 7.5 web server to pass the BEAST PCI vulnerability compliance scans
If your e-commerce website keeps flunking PCI vulnerability complaince scans with the following error:
BEAST (Browser Exploit Against SSL/TLS) Vulnerability, CVE-2011-3389
and you are running Microsoft Server 2008 R2, I can help you.
If you aren’t on Windows Server 2008 R2, there is no known way to pass this test short of upgrading your server to W2K8R2 and doing the following steps.
This is the exact vulnerability as reported (in our case, by Trustkeeper):
BEAST (Browser Exploit Against SSL/TLS) Vulnerability The SSL protocol encrypts data by using CBC mode with chained initialization vectors. This allows an attacker, which is has gotten access to an HTTPS session via man-in-the-middle (MITM) attacks or other means, to obtain plain text HTTP headers via a blockwise chosen-boundary attack (BCBA) in conjunction with Javascript code that uses the HTML5 WebSocket API, the Java URLConnection API, or the Silverlight WebClient API. This vulnerability is more commonly referred to as Browser Exploit Against SSL/TLS or “BEAST”.
CVE: CVE-2011-3389
NVD: CVE-2011-3389
Bugtraq: 49778
CVSSv2: AV:N/AC:M/Au:N/C:P/I:N/A:N(4.30)
This is the remediation (as stated by Trustkeeper):
Affected users should disable all block-based cipher suites in the server’s SSL configuration and only support RC4 ciphers, which are not vulnerable to fully address this vulnerability. This vulnerability was addressed in TLS version 1.1/1.2, however, support for these newer TLS versions is not widely supported at the time of this writing, making it difficult to disable earlier versions.
Additionally, affected users can also configure SSL to prefer RC4 ciphers over block-based ciphers to limit, but not eliminate, exposure. Affected users that implement prioritization techniques for mitigation as described above should appeal this vulnerability and include details of the SSL configuration.
Here is the evidence (as stated by TrustKeeper):
Service: http
Evidence:
Cipher Suite: SSLv3 : DES-CBC3-SHA
Cipher Suite: SSLv3 : RC4-SHA
Cipher Suite: SSLv3 : RC4-MD5
Cipher Suite: TLSv1 : AES256-SHA
Cipher Suite: TLSv1 : AES128-SHA
Cipher Suite: TLSv1 : DES-CBC3-SHA
Cipher Suite: TLSv1 : RC4-SHA
Cipher Suite: TLSv1 : RC4-MD5
That isn’t much help, of course.
Ok, here is how to solve this. And you don’t even need REGEDIT!
- Make sure your website is on a Windows 2008 R2 server, with a valid SSL certificate.
- Download the following FREE – and FANTASTIC program to your web server.
- Run the program on your web server. Please be logged in as full admin, and remote desktop is fine.
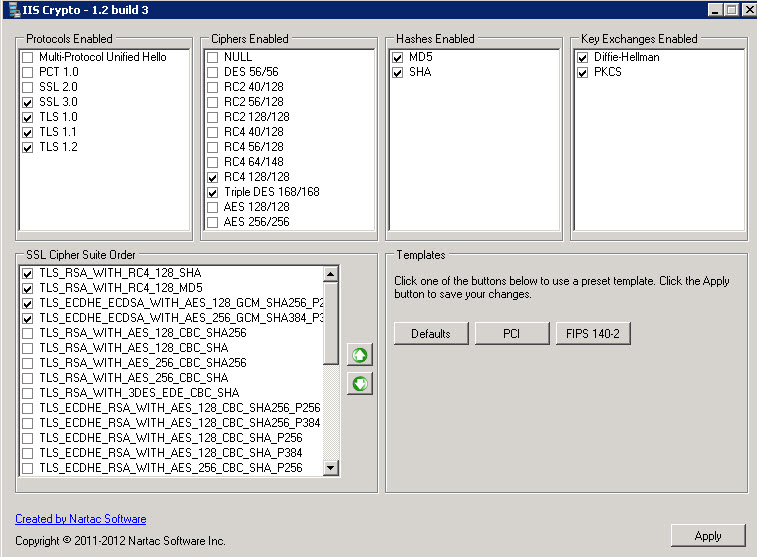
- Start by clicking the PCI button, then make all your settings look like below:
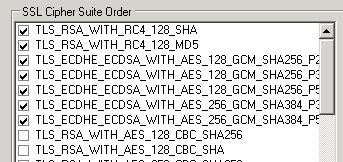
- In some cases you might have a few more listing under SSL Cipher Suite order. Here is a screenshot from a second server (below). The settings below are also perfectly fine:
- In all cases – MAKE YOUR SETTINGS JUST LIKE ABOVE – and your site should always pass the BEAST test.
- IT IS CRITICAL that you have ONLY the CIPHERS selected in the above two screenshots, and the TOPMOST TWO in THIS SPECIFIC ORDER.
- apply the changes
- Restart the server.
- once the server is back up and running, go to the website below:
- Allow the test to complete. The test will tell you if the site passes all the tests and is BEAST compliant, and it will give you a score for your website. The website we tested scored 89 which is an “A”.
Hopefully this will help shortcut this process for some of you. I literally spent hours working this solution out.

HI
I would like to thank you for this blog – it helped greatly. Just to let you know that the program mentioned in your blog has got a button to fix the BEAST issue specifically. It would be helpful for other to update your blog.
Kind Regards
Sandeep
Sandeep,
You are correct, there is a new button in v1.3 of the app called BEAST which is supposed to auto-fix things. Just be sure after you hit that button (and restart) and re-scan for complaince, that if it DOES NOT pass you go through the rest of my settings and adjust those manually. Since I have yet to try the new 1.3 version you may need to make additional changes to get them inline with what I posted in the above post to pass compliance. Thanks again for your feedback and glad that I was able to help you.
I ran that tool and after restart I cannot connect via remote desktop. It did warn me about it, but I wasn’t sure what I was supposed to do. Everything else works on the machine, except for RDP. Thoughts?
Run the tool again, and don’t use the BEAST button if that is what you did. Instead look very closely at the choices I manually made (since my post was before they added the BEAST button). The choices I made on the screenshot will permit RDP (which was required for my setup). I had the same problem during my trial and error process and I am pretty sure it was due to missing protocols in the upper left box. Additionally look at the provider order on the lower left box and make sure they are ordered correctly and “at the top” rather than mixed in. Lastly after you make the changes make sure you reboot the machine and re-test it again. I am able to access my machines via RDP using the exact settings pictured in my screenshots. Thanks for your comments.
I made it exactly like you did. It passes BEAST (although I think I got a higher score when just clicking the BEAT button, but I’m not sure) but I still can’t RDP. Thankfully I have KVM and I’m able to make changes. I will play it with some more later. Now I need the server to be functioning. Thanks.
I will do some further looking and experimenting into this. Thanks for your feedback.
Under Remove Desktop Session Host Configuration I had the encryption level set to “FIPS Compliant”. Using your settings, but setting it to “High” instead allowed me to RDP. I hope this helps.
Thank you again for the follow-up. We’ll keep all this info here for people who might need it in the future.
After running the tool I had a problem connecting to my server with RDP as well. The suggestions above did not resolve my issue and prior to applying the changes in the tool, I tripled checked that my screen looked like the screenshots above. The resolution for me was to go under terminal services configuration and change the security layer for the RDP-Tcp connection from Negotiate to RDP Security Layer. Once I did that I was able to connect via RDP.
I do have another issue however. After running the tool, I am no longer able to service browsers requests on the server. Any suggestions for resolution?
Hi,
thanks for pointing out to that tool, really helpful.
If there is any wrong behaviour, its mainly because someone clicked too much/too few of the checkboxes mentioned in the post 😉
Pingback: After Windows Update KB 3061518 many websites stop working in IE « rakhesh.com
Pingback: How do I disable TLS 1.0 without breaking RDP? – Internet and Tecnnology Answers for Geeks
Pingback: How do I disable TLS 1.0 without breaking RDP? * VPN SSL Online
Pingback: Configure IIS Web Server for PCI DSS Pass | Toyin Ogunmefun's space